By Sylvia Lorico
Received any suspicious emails recently? Ryerson email accounts have been the target of phishing scams and students should learn how to identify them.
Phishing is the practice of sending emails appearing to be from reliable sources in order to trick users into sharing personal information such as credit card numbers or passwords.
Once the people who send phishing emails have access to this information, they can potentially harvest confidential information from within an account, use it to send more spam emails, open new bank accounts, make purchases and even hide criminal activity.
Phishing is a common risk worldwide. According to a 2014 Symantec Internet Security Threat Report, the global rate of phishing is about 1 in every 392 emails. The report studied internet security threats including phishing during the 2013 year.
Brian Lesser, Chief Information Officer at Ryerson, said the reason some people may fall for phishing comes down to their behaviours.
“People are used to skimming what they read and doing what they’re told,” he said. “In a sense, they believe what they read.”
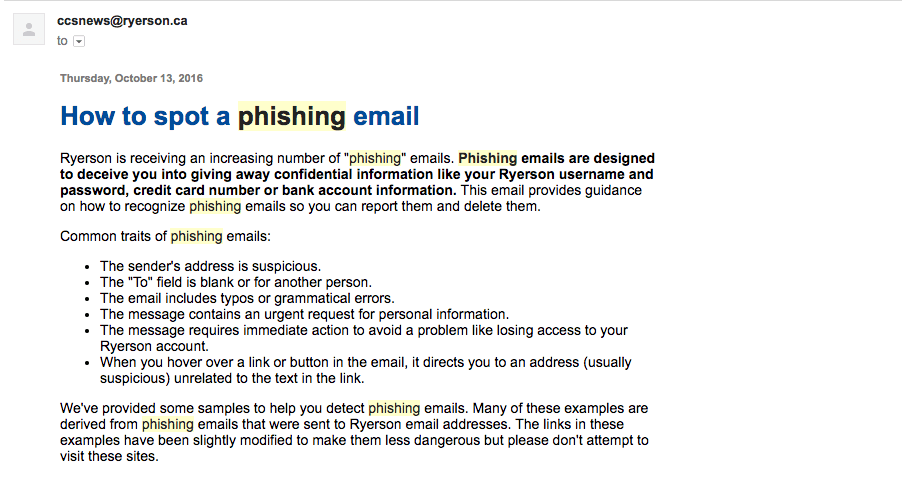
The Ryerson Computing and Communication Services (CCS) has a page on their website which helps users distinguish phishing emails from legitimate emails. Common traits of phishing emails include suspicious sender addresses, typos or grammatical errors, a blank “To” field in the email, an urgent request for personal information as a solution to an immediate problem, and a link which will direct you to a misleading website.
Currently, there are no statistics for the total number of Ryerson students who fall for phishing. Lesser said students don’t often report suspicious emails directly to Ryerson. There is an option on a student’s Gmail account to mark an email as a phishing attempt, but the report is sent to Google, not Ryerson.
Ryerson does not have a system to distinguish phishing emails from spam. Items marked as suspicious are not further filtered to separate spam emails from phishing emails.
Instead, once an email is determined as potentially phishing, Ryerson’s firewall will block on-campus access to the site(s) it links to.
Phishing for Ryerson students
On Dec. 22, a phishing email was sent to 750 Ryerson emails. The sender, who claimed to be from McGill University, tried to get students and staff to log into their Ryerson accounts through a false login page that was almost identical to the Ryerson login page. The sender claimed there was a security incident on campus and encouraged users to click on a link.
Within 30 minutes of the email being sent, 11 people clicked on the link in the email and three users logged in with their Ryerson password. By the time the site was blocked by the firewall, 16 people in total had clicked on the link and four had logged in with their passwords.
“We’re used to seeing the security incident reports on our emails that we click on it without thinking,” Lesser said. “But if we had looked at the email closely, we would see that it was not, in fact, a security report.”
It is important to note that the numbers from Dec. 22 only apply to users who were on campus at the time. They do not include users who potentially accessed the email outside of Ryerson premises.
On the Ryerson CCS website, students are told to report phishing emails to spamrec@ryerson.ca. This helps the CCS identify and warn the Ryerson population about potential phishing. They also encourage users to delete the emails without clicking on their hyperlinks or attachments.
Ryerson performs phoney phishing to educate staff and students
There is an initiative underway to educate Ryerson account-holders about phishing. Last October, Ryerson IT sent fake phishing emails to deans, executives and other employees in order to determine how many people fall for them. If they fell for the email, they were directed to a page on how to detect phishing.
The test, which occurred from Oct. 16 to Oct. 20, sent out fake phishing emails to 1,555 Ryerson employees. They focused on deans, executives and other employees who were most vulnerable because they held important confidential information that could be compromised.
Two weeks prior to the test, Ryerson CCS sent emails to their employees announcing the deceptive email training. An email was then sent to all staff and students the week before the test informing them how to spot phishing.
The test showed that about 16 per cent of recipients fell for the fake phishing emails in the first test.
After two more additional tests on Nov. 7 and Nov. 21, the percentage of people fooled went down to eight per cent.
This statistic is close to the national average. According to an August 2011 report submitted to Public Safety Canada by Ekos Research Associates, about seven per cent of Canadians have unknowingly replied to spoof or phishing mail.
There is a proposal within the CCS to send the fake phishing emails to all staff and students in the future.
“People desperately need education,” said Lesser. “Training is hard because you’re fighting years of acculturation in a point and click kind of world. The best thing we can do is to make people really cautious and suspicious of what they read and get them to systematically check it.”











Leave a Reply